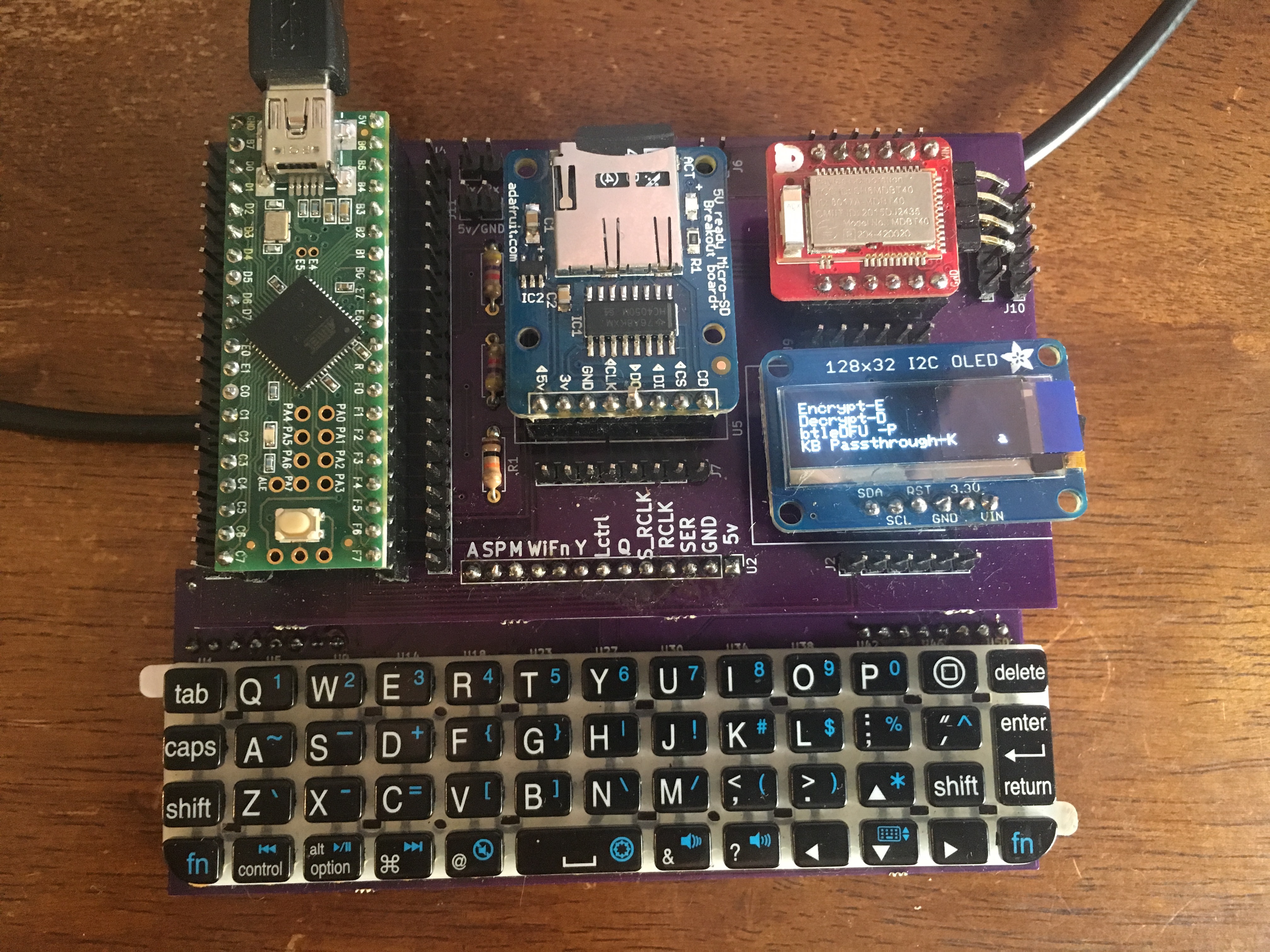
Sheath Mobile Encryptor
Sheath works off the idea that you can only truly trust a device with sensitive information if you can verify it's inner workings and control how and when it allows information in and out of it. Sheath achieves this by using a simple micro controller to handle the encryption. The eventual goal is to use a microcontroller with open silicon and freely available schematics. Messages can be typed into the device, encrypted, then sent to a phone or computer over BT Low energy or usb so that the message can then be transmitted over any unsecured channel. For receiving and decrypting messages, Sheath uses the same APIs smart watches use to automatically receive messages and present them to the user so that they can be decrypted and read on the built in LCD. The problem is many modern computers (and mobile phones) have numerous security flaws, some known and some unknown. Closed source CPUs may have untrustworthy, always-running potential backdoors (Intel ME), or simply have a backdoor hardcoded into them (Allwinner ARM cpus for many years). Even many open source operating systems require precompiled close source code (blobs) in the form of firmware in order to run on modern hardware. Unfortunately, building a verifiably trustworthy modern computer is nearly impossible. Instead of building an entire computer, Sheath is an attempt to build a trustworthy and verifiable device for the most important segments of computer use, encryption and password storage. By removing any ability for the device to connect to the internet, and providing open access to schematics and source code for all of the logic components, Sheath provides a verifiably trustworthy encryption and decryption. Sheath is in the prototype stages. The keyboard works for text entry, it can encrypt text, decrypt text, receive notifications from devices, and act as a keyboard to enter the encrypted text into the phone or computer to make offloading encryption to sheath as painless as possible without compromising security. Potential issues: Sheath does not protect your metadata. Full protection of metadata isn't really possible at this point while still communicating over the internet, however you can minimize it through the use of certain decentralized messengers. Heres a picture of Sheath so far: